Imagine having a digital ledger at your fingertips, one that is both incredibly secure and transparent, where information is shared and verified without the need for a middleman. That’s the power of blockchain, and it’s revolutionizing how we think about data and transactions in the digital age.
A blockchain is a distributed database that maintains a continuously growing list of records, called blocks, which are linked and secured using cryptography.
Each block contains a timestamp and transaction data, which is not alterable without altering all subsequent blocks. This structure creates an indisputable record of transactions, providing transparency and security to all participants. Fortunately, these qualities are prime for technology that disrupts the current banking system.
A quick note before we get started: there is a lot of terminology in this post. We do our best to explain it as it comes up, but most of it should also be clickable to take you to a page that gives you far more info about it. We also have a glossary that explain not just the technical terms but also crypto lingo like “degen” and “wagmi” that you can check out if you’re interested.
Introduction to Blockchain Technology
You’ve likely heard the term “blockchain” thrown around, especially when people talk about cryptocurrencies like Bitcoin. But blockchain is much more than just a part of digital currencies. It’s a groundbreaking way of keeping records that is different from traditional systems you’re used to.
Think of a blockchain as a digital ledger. If you’ve ever seen a ledger in a store, it’s a book where all sales and purchases are written down. Now, imagine this ledger is not in one place, but copies of it are spread out over many computers around the world. The purpose of this is to ensure one centralized entity can’t:
- Create fake transactions
- Remove true transactions
- Being vulnerable to attacks that would enable the above actions
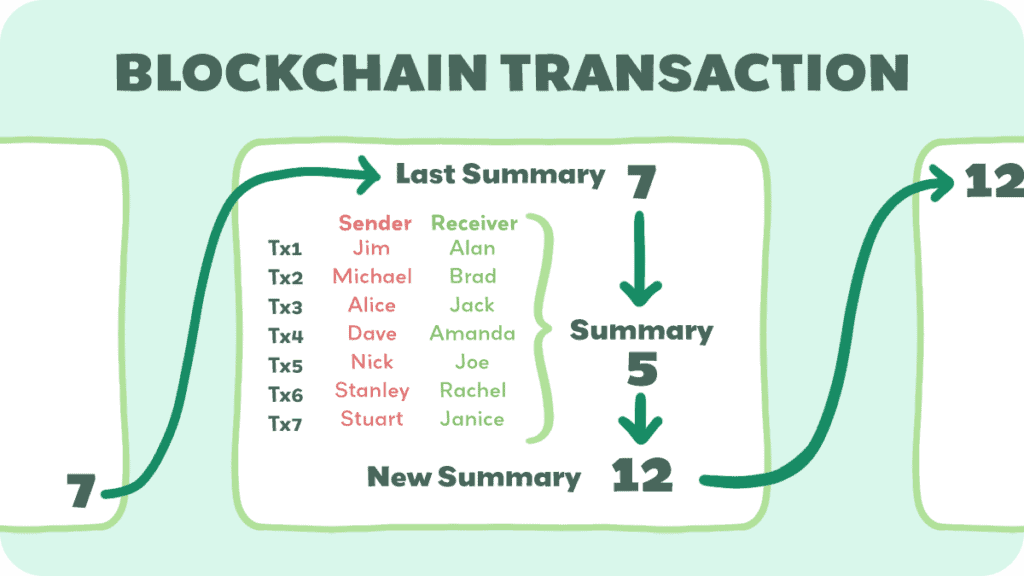
Each time a transaction happens, everyone’s ledger updates. This is what we mean when we say blockchain is distributed. Nobody owns the whole thing, but everyone who uses it has a copy of it.
What makes blockchain special is how it records information. It’s like an unbreakable chain. When someone enters a transaction, it gets locked in a block with a unique lock, what we call cryptography.
Once the block is full, it links to the previous block, forming a chain. This chain is incredibly secure because to change even the smallest detail anywhere in the chain, you would have to break the locks on all the following blocks. These “locks” are actually mathematical formulas that are extremely difficult to solve, and we’ll get to that soon.
This chain of interlinking “locks” are why blockchains are so trustworthy.
History of Blockchain Technology
Most people think the idea of blockchain started with a person (or perhaps a group of people) known as Satoshi Nakamoto.
But, the concepts foundational to blockchain technology didn’t just emerge out of the blue with Satoshi Nakamoto’s whitepaper in 2008. They are the result of years of work and thought from various computer scientists and cryptographers.
The story begins in the early 1990s with researchers Stuart Haber and W. Scott Stornetta. They were tackling a problem of how to timestamp digital documents so that it couldn’t be tampered with—a concept crucial to the integrity of digital records.
They developed a system where each document was cryptographically secured with a timestamp. Each new timestamp included the previous timestamp’s information, creating a chain of time-stamped records.
In 1991, they incorporated Merkle trees to their design, which greatly improved the efficiency of the system. This meant they could collect many documents into one block and generate a single hash — a string of numbers and letters that uniquely identifies a set of data.
These developments laid the groundwork for what would eventually be known as a blockchain.
The ideas continued to develop in the cryptography community, which is a group of people interested in the art of writing and solving codes.
Within this community, a movement called the “cypherpunks” was growing. This was a group of activists advocating for the widespread use of strong cryptography and privacy-enhancing technologies as a route to social and political change.
They were interested in using cryptography to create secure systems that were beyond the control of any one entity — a core principle that would be vital to blockchain technology.
It wasn’t until two decades after Haber and Stornetta’s work that Satoshi combined these ideas with a proof-of-work system to create Bitcoin’s blockchain.
This was the first time the concept of a blockchain was used in such a practical and innovative way, leading to the popular field of blockchain technology we see today.
Satoshi introduced the world to Bitcoin, and with it, the first real-world blockchain. The goal was simple: allow people to send and receive money over the internet without needing a bank in the middle.
Before blockchain, sending money online was like handing cash through a series of checkpoints, each taking a little fee and needing trust.
Satoshi’s vision was different. With blockchain, you could send money directly to someone else, no checkpoints needed. This idea was revolutionary. It meant that people had complete control over their own money, without any bank or government telling them what they could or couldn’t do.
As Bitcoin grew, so did the technology behind it. People started to see that if you could use blockchain for money, you could use it for other things too, like contracts, voting, or proving ownership.
This is how blockchains began to spread and evolve, forming the foundation for countless new innovations and applications beyond just cryptocurrency.
It marked the start of what many call the “blockchain revolution,” setting the stage for a future where technology puts power back into the hands of the people.
How Blockchains Work
Let’s get into the technical side of blockchains. If you’re more interested in other aspects, like the blockchain trilemma, scaling, and other use-cases, you’ll want to scroll down as we get into that a little later.
You can think of a blockchain as a train with many carriages, which we call blocks.
Blocks
Each block carries data, just like a carriage might carry cargo or passengers. Usually, such as on the Bitcoin blockchain, this is a list of transactions.
Every time a new transaction happens—like if you were to send money to a friend—it’s like adding a new piece of cargo to the carriage. The carriage is the “block”, while the packages are the “transactions” inside that block.
For example, it might look like this:
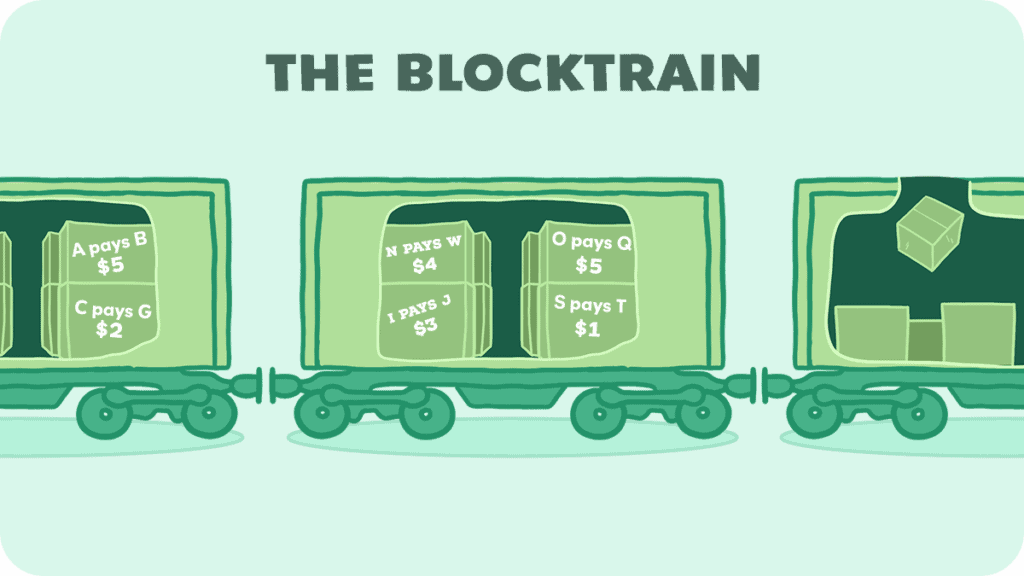
If we’re dealing with Ethereum, the contents of a block are mostly transactions, but it can be a few other things, like smart contracts, which are really neat (but we explain them a bit later).

For other alt-coins the blocks can contain information like the usage of your WiFi, or files, or documents. Nonetheless, a block is just a collection of data.
These blocks have limits, meaning they can only have so many transactions (or other data), so we have to continually add them. For our example, Bitcoin’s block size is limited to 1MB of data, which is around 2000 transactions. The amount of transactions in a block can change, based on how many people want to perform transactions.
Since these blocks have a limit, the price to put information in them is generally correlated to how popular the blockchain is.
These blocks fill up and then we have to do something with them.
That “something” is to add them to the blockchain. Remember, in our analogy, the blockchain is an ever-growing train.
Consensus
Now, before a new block can be added to the train, it must be verified by everyone at the station. This process is called consensus, and it’s vital because it ensures that everyone agrees on the transaction’s details.
Technically, you can add a block to your own copy of the blockchain, but if everyone else doesn’t agree on it (or reach consensus), then it’s not really part of the true decentralized blockchain.
Different blockchains use different consensus mechanisms to ensure everyone agrees on how the next block is added. Let’s look at some of the most popular ones.
| Consensus | Description | Example |
| Proof of Work (PoW) | In Proof of Work, miners solve complex mathematical problems to validate transactions and create new blocks. The first miner to solve the problem gets to add the block to the blockchain and is rewarded. | Bitcoin |
| Proof of Stake (PoS) | Proof of Stake selects validators in proportion to their quantity of held cryptocurrency. Instead of mining, you ‘stake’ your coins to be selected to validate transactions and create new blocks. | Ethereum |
| Delegated Proof of Stake (DPoS) | In DPoS, coin holders vote for a few delegates who are responsible for validating transactions and maintaining the blockchain’s integrity. It’s a more democratic form of PoS. | EOS |
| Proof of Authority (PoA) | Proof of Authority is a reputation-based consensus algorithm where validators are pre-approved and deemed trustworthy by the network. | VeChain |
| Proof of Space (PoSpace) | Proof of Space allows the blockchain network’s participants to use the empty space on their hard drives to participate in the consensus process. | Chia |
| Proof of Burn (PoB) | In Proof of Burn, miners send coins to an unspendable address to “burn” them. This gives them the right to write blocks in proportion to the coins burnt. | Slimcoin |
To help explain how all this works, we are going to stick with a record of transactions, like in Bitcoin. Specifically, we call this record a ledger, because the only data we’re storing is value exchanging hands.
So far, we know that Bitcoin has blocks that contain transaction data, and one block can hold about 1MB of data. We know that when the block is full, we need to all agree that the content is accurate, lock it up, and add it to the blockchain.
Let’s zoom in on the part when the block gets full.
What do we do with these blocks once they are full? We add them to the network. How do we do that? Well, we “mine” them, and since Bitcoin is a “proof-of-work” model, we have to prove that we mined them. This includes a lot of complex math, which brings us to something called a hash.
A hash is the “lock” we were talking about earlier.
Hashing Function
A hashing function is a special kind of computer process that takes any form of data—like a message, a file, or even a whole book—and crunches it down into a specific size of numbers and letters, called a hash.
This hash is unique to the original data. If you change even a tiny bit of the original data and run it through the hashing function, you’ll get a completely different hash. This means that hashes aren’t predictable. The only way to get a hash is to compute it.

Here’s how it works:
- You input the data into the hashing function.
- The function performs complex mathematics on the data.
- It produces a hash, which looks like a long string of random characters.
An important feature of a good hashing function is that it’s irreversible. This means you can’t take a hash and work backwards to find the original data.
Let’s look at a specific example using the SHA-256 hashing function, which is used by the Bitcoin blockchain. Imagine you have the word “hello”. If you put “hello” through the SHA-256 hashing function, it will always produce the same long string of characters:
2cf24dba5fb0a30e26e83b2ac5b9e29e1b161e5c1fa7425e73043362938b9824
But if you change just one letter, say “hello” to “Hello”, you’ll get a completely different hash:
185f8db32271fe25f561a6fc938b2e264306ec304eda518007d1764826381969
This consistency and unpredictability make hashing functions incredibly useful for blockchain and security purposes. When a new block is created in a blockchain, the transactions are hashed, and the resulting hash is included in the block. Then, the entire block (and all the data in the transactions) is hashed, and that hash is used in the creation of the next block, creating a secure chain.
If someone tries to change a block that was “mined” in the past, that block’s hash will be changed, and due to that, it will stick out like a sore thumb, because all the other blocks tied to in the future will be wrong:
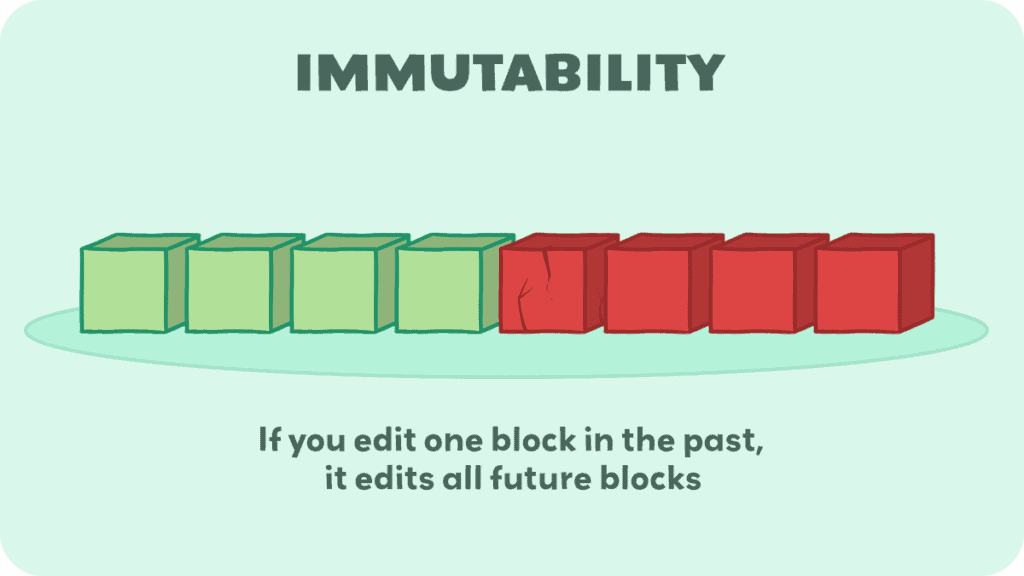
All the data is tied together mathematically. This is where the part “chain” comes from. The technical term for this is “Immutability“.
Essentially, the Bitcoin blockchain needs people to figure out the block’s hash, and computers and mining farms all around the world are all “mining” away to find the right number. When they do find it, we say that the block is “solved” and “verified”.
For context, a “block” is solved in Bitcoin when a random number is added to the block transactions, and then a certain number of leading “0”s has been achieved based on the difficulty. The difficulty is adjusted throughout time, based on how many people are mining. More miners = more “0”s needed.

As a quick side note, mining can be a big upfront cost. You have to buy the hardware and have enough electricity to run it. For a blockchain as big as Bitcoin, if you are the “solver”, you win a certain amount of BTC.
However, there are thousands of miners competing against each other, and on average a block is mined every 10 minutes. This means your chances of solving a block are very low.
The thing most people do is join a mining pool.
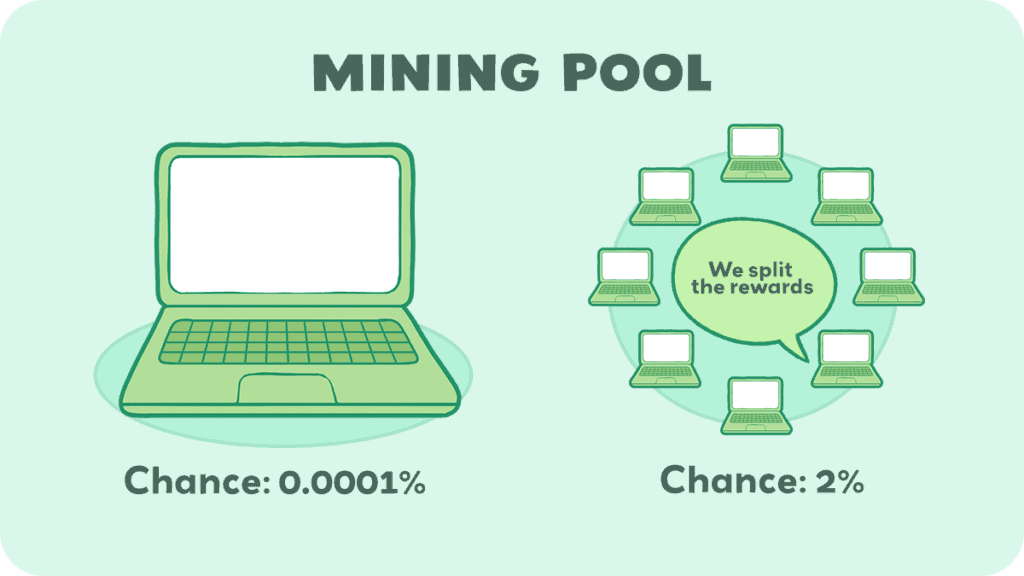
A mining pool is a group of cryptocurrency miners who combine their computational resources over a network to strengthen their chances of finding a block or mining a cryptocurrency. Here’s how it operates:
- Combining Resources: Individual miners, with their own mining hardware, connect over the internet to a pool server.
- Working on the Puzzle: The mining pool server breaks the complex problem into smaller pieces and distributes the work among the pool members.
- Sharing the Rewards: When one of the miners in the pool successfully mines a block, the reward is distributed among all members of the pool, usually based on the amount of computational power each contributed.
Speaking of hardware, there is a specific kind of tech that is built for mining. It’s called “Application-Specific Integrated Circuit”, or ASIC miner for short. While a regular computer can perform all sorts of tasks, an ASIC miner is a computer that has been designed to focus solely on mining cryptocurrency. It does this one job extremely efficiently. These can be pretty expensive though, partly due to research and development costs.
We actually have a document that helps you calculate the starting cost of mining and how long you would have to mine to make more than you put in, and a video that explains it. You can check that out on its own page.
Now let’s see how hashing and mining—or the equivalent—works with other consensus mechanisms.
Hashing in Proof of Stake (PoS)
In Proof of Stake, validators are chosen to create new blocks based on the amount of cryptocurrency they hold and are willing to “stake” as collateral.
Here’s where hashing comes in:
- Random Selection: Hashing can be used to help choose the next block creator. Often, the current state of the blockchain, which includes many previous hashes, is used as an input to a hashing algorithm to ensure a degree of randomness in the selection process.
- Verifying Transactions: Before a block is finalized, all transactions within it are hashed to ensure their integrity. This hash, along with others, will contribute to the cryptographic security of the entire blockchain.
Hashing in Other Consensus Mechanisms
- Delegated Proof of Stake (DPoS)
- Similar to PoS, hashing is used for ensuring the integrity and order of transactions within blocks. It may also be part of the process for electing delegates.
- Proof of Authority (PoA)
- Validators are pre-selected and trusted entities. They still use hashing to create a unique fingerprint for each block, ensuring tamper-evident records.
- Proof of Space (PoSpace)
- Hashing is utilized to prove that the prover is allocating a certain amount of storage space to the network. Here, the focus is not on computational power, as in PoW, but on space availability.
- Proof of Burn (PoB)
- Participants send coins to a verifiable unspendable address. These transactions, like all others, are hashed and recorded on the blockchain, symbolizing a “burn” of coins.
In each consensus mechanism, hashing serves the critical purpose of securing the blockchain.
Whether it’s used for creating new blocks, like in PoW, or ensuring the integrity of transactions, like in PoS and others, hashing ensures that data is not altered and remains consistent across the entire network.
This immutable characteristic is what makes blockchain technology particularly robust and trustworthy.
Cryptography
Speaking of trustworthy, there are a few things we expect from a blockchain.
You might have heard the word “cryptography” associated with secret codes and spies. In the world of blockchain, it’s not about sending hidden messages, but about creating a secure digital environment.
Encryption & Decryption
Cryptography uses mathematical algorithms to transform information into a secure format that only someone with a special key can unlock. Think of it like a secret code where only you and the person you trust have the decoder ring. In blockchain, this is used to secure transactions and control who has access to funds.
Digital Signatures
Each time you make a transaction on a blockchain, you use a digital signature. This signature proves that you are the one who agrees to the transaction — like signing for a package that arrives at your door.
It uses a combination of your private and public keys, which are long strings of numbers and letters generated by cryptographic algorithms. These keys are essential for cryptocurrency wallets to work.
Public and Private Keys
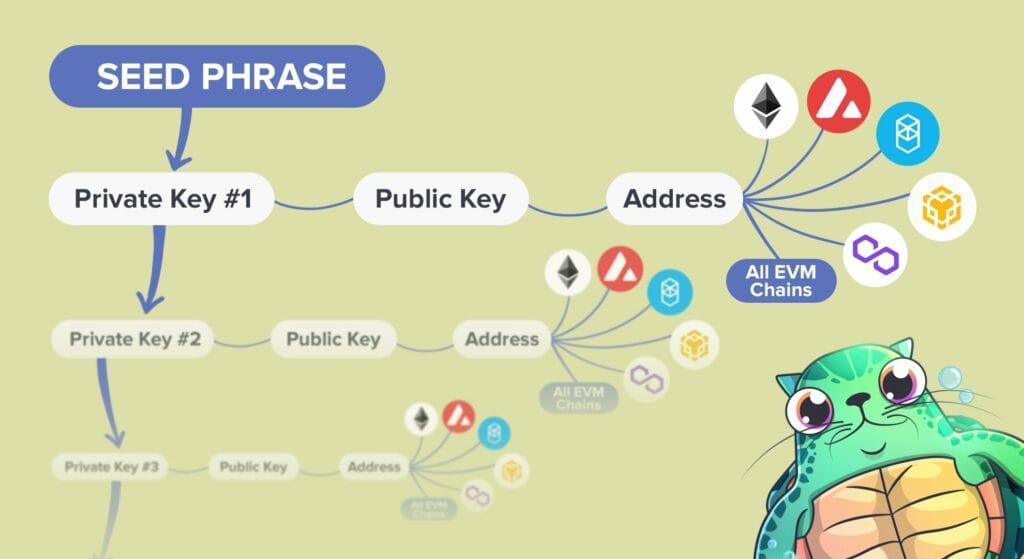
Your private key is your personal secret code, and you should guard it like a treasure. It’s what you use to access your cryptocurrency and sign off on transactions.
Your public key, on the other hand, is like your mailbox address. Anyone can know it, and it’s how people send you blockchain transactions. The beauty is, even if someone knows your public key, they can’t fake a transaction as you without the private key.
Note: In many cases, users have an address, which is usually a shorter version of the public key.
Many chains use the same public key, private key, and address format, meaning you can use the same “account” on different chains. Other times, chains will develop their own format, requiring you to create a new “account” with a new private key format. Generally, the seed phrase (which is responsible for creating many different “accounts”), will work with many blockchains.
For example, Bitcoin and Ethereum have different key formats. A private key for a Bitcoin account will not work on Ethereum. You can use the same seed phrase to create respective accounts on each network, though.
Hash Functions in Cryptography
Remember the hashing we talked about? It’s also a part of cryptography. Hash functions are special because they work one way. You can turn the message into a hash, but you can’t turn the hash back into the original message. This is crucial for maintaining the integrity of the blockchain, making sure that once data is recorded, it can’t be tampered with.
Layer 2s and Sidechains
Another important thing to remember about blockchains is that they can have many layers. These layers try to address the challenges faced in the blockchain trilemma, which we explain below. But briefly, the trilemma is that a blockchain needs to balance security, scalability, and decentralization, and it’s basically impossible that a single layer successfully addresses all three.
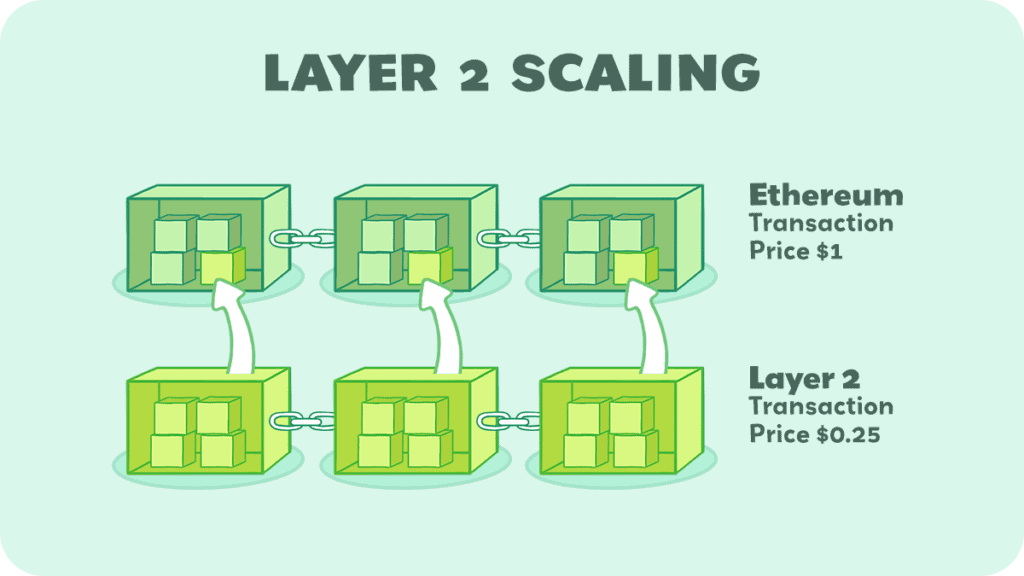
You don’t need to know why that is right now, as we talk about it later, but just know that other layers are sometimes needed to help balance it.
For instance, layer 2s on Ethereum, such as Arbitrum and Optimism, are meant to help the network scale while keeping transaction fees low. Transactions on Ethereum in 2021 got as expensive as $200 each. So layer 2s let you do transactions that use Ethereum’s security and decentralization but for cheaper.
Both layer 2s and sidechains are solutions designed to extend the capabilities of a primary blockchain, but they do so in different ways:
Layer 2s
Layer 2s are protocols built on top of an existing blockchain (the “base layer” or “layer 1”) to improve its scalability and efficiency. They handle transactions off the main chain, reducing the burden on the network. Here’s how they work:
- Offloading Transactions: Transactions are processed on a separate layer, which is faster and more cost-effective.
- Security: They still inherit the security guarantees of the main blockchain because the transactions are ultimately settled on layer 1.
- Examples: The Lightning Network for Bitcoin and Rollups for Ethereum are popular layer 2 solutions.
What are Rollups?
Rollups are a layer 2 scaling solution for blockchains, and they’re like a high-speed train that runs parallel to the main railway tracks. They handle a lot of the passenger traffic (transactions) quickly and efficiently, then report back to the main line (the main blockchain).
Rollups process and store transaction data off the main blockchain but post transaction data back onto it. Here’s the breakdown:
- Off-Chain Aggregation: Transactions are grouped together and processed off-chain, which means outside of the main blockchain.
- On-Chain Data: Only the transaction data or its cryptographic proof is posted back on-chain. This ensures the main blockchain knows the transaction happened without having to do all the processing work.
- Smart Contracts: Rollups use smart contracts on the main blockchain to manage the input and output of transactions from the rollup system.
There are mainly two types:
- Optimistic Rollups: They assume all transactions are valid by default and only run computations if a transaction is challenged.
- Zero-Knowledge Rollups (ZK-Rollups): They provide cryptographic proof that transactions are valid, which the main blockchain checks for confirmation.
You might be thinking that rollups sound like a good way to get more private transactions, since they don’t post their activity to the main blockchain, just proof that it occurred. If you’re thinking that, you’re right and you’ve obviously been paying attention so far!
Privacy-focused chains are specialized blockchains that prioritize the confidentiality of transaction details and user identities. Unlike traditional blockchains where transaction details are openly visible, privacy chains use various cryptographic techniques to obscure this information.
Another way to get privacy is through the use of mixers, also known as tumblers. These work by pooling and scrambling cryptocurrencies from multiple users to obscure the trail leading back to the original source.
There’s a lot of detail we go into in our post about privacy, so be sure to check that out if you’re curious about ring signatures, stealth addresses, confidential transactions, and more!
Sidechains
Sidechains are separate blockchains that run alongside the main blockchain, with their own independent ledger and consensus algorithm. They are connected to the main chain via a two-way peg, allowing assets to be transferred back and forth between the two chains. Here’s what they offer:
- Independence: Sidechains operate independently of the main chain, which means they can have different block times, consensus mechanisms, or privacy features.
- Resource Allocation: They help in distributing the transaction load, but they don’t necessarily inherit the security properties of the main chain.
- Examples: Liquid Network for Bitcoin is an example of a sidechain.
Who Maintains the Blockchain
We’ve talked about how the blockchains worked, and we mentioned that people all over the world participate in mining, staking and the other consensus mechanisms. But how does that actually work? How does someone maintain, or participate in, the blockchain?
It’s not a very straightforward answer, because it depends on the blockchain you’re interested in using. But let’s go over some of the basic concepts that apply to all blockchains.
Nodes
Remember how blocks are like ledgers that record and store data? Every block contains:
- Transaction Data: This is a record of all transactions completed in a certain time frame.
- A Hash: Each block has a unique code called a hash. It’s like a fingerprint, ensuring the block’s contents haven’t been tampered with.
- The Previous Block’s Hash: This links blocks together in a chain, creating a secure and unbreakable sequence from the first block to the latest.
All of this data has to be stored somewhere, and the people who choose to participate in maintaining the blockchain, through mining, staking, or otherwise, are called node operators.
Nodes are just computers that:
- Store the Blockchain: Nodes hold copies of all the blocks.
- Validate Transactions: They check to make sure that transactions are legitimate and follow the rules of the blockchain, otherwise they alert their connections
- Maintain the Network: Nodes communicate with each other, sharing new transactions and blocks so everyone has the same, up-to-date ledger.
A really important part of a blockchain is how many nodes there are, and how spread out they are. This distribution is called decentralization.
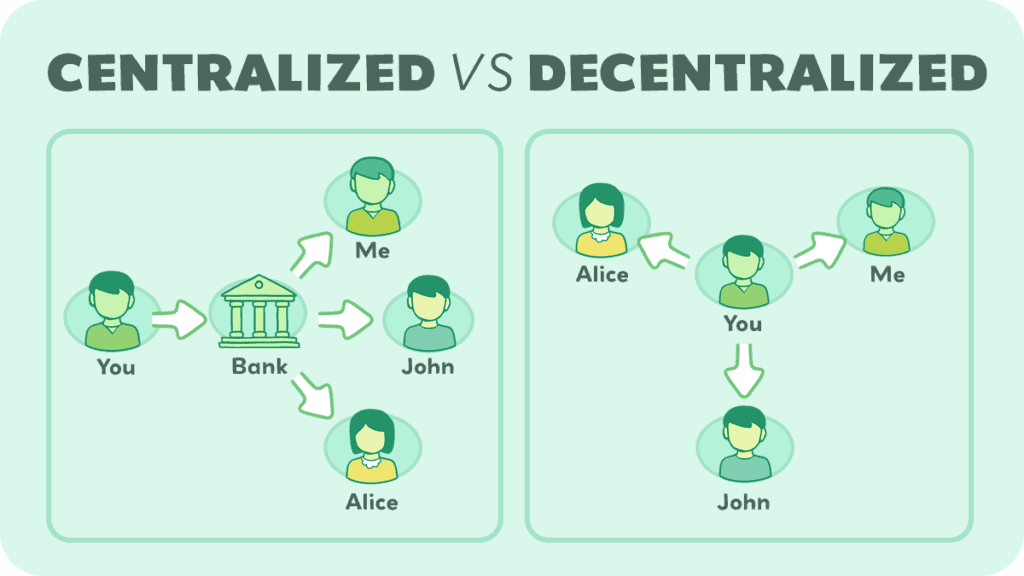
Decentralization
This doesn’t have to be confusing, so think about it like this. Centralized means one person controls it. For example, your grades in high school… only your teacher had access to add in your grades and change it. They could flunk you if they didn’t like you, and nothing personal here, but maybe you just didn’t understand what they were teaching because they sucked at teaching.
Decentralized means more than one person can have access to your grades. Imagine if all of your classmates were allowed to look at your answers and give you a grade based on your papers and tests. Imagine if they could vote on what grade you got, instead of your teacher.
This is essentially what decentralized means. Instead of one person having a list of all the bitcoin transactions, literally anyone who wants to have them can have them and look at them and point out any red flags.
Not only that, and this is the important part, but anyone can mine and actually vote on the blockchain. This means they can say “Bill really did pay John $50”.
Or, they could make fake transactions and say “John paid Bill all of his money”. The problem of fake transactions is solved by using cryptocurrency wallets.
It should be noted that on most blockchains, you can’t actually create fake transactions due to a special “stamp” that someone puts on a transaction, which can be checked mathematically to prove they are who they say they are.
However, a 51% attack would allow the attacker to choose which new transactions could be confirmed, not edit past transactions. A 51% attack is when more than half of the nodes on the network agree to act in a malicious way.
Basically, the more nodes you have, the more secure the network is. Just like if you have ten policemen in a bank, it’s harder to rob the bank than if you only had one policeman; if you have hundreds or thousands of nodes on a blockchain, then you are increasingly less likely to let something malicious happen on the blockchain.
What happens then? What if some people want the blockchain to show a particular history and others don’t? Then they could decide to fork the chain.
Blockchain Forks
Forking in blockchain happens when there’s a change or upgrade in the protocol, and the chain splits into two separate versions. It’s like a road that divides, where one path follows the old ways and the other adopts a new direction.
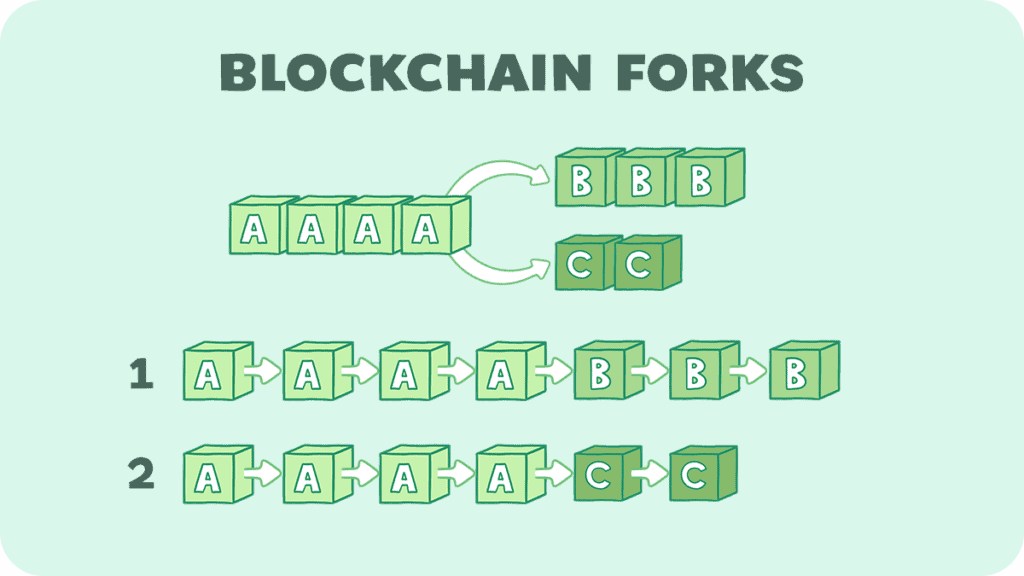
There are two main types of forks: soft forks and hard forks.
Soft Fork
A soft fork is a software upgrade that is compatible with the older version. It’s like adding a new rule in a game that doesn’t change how it’s played for those who don’t adopt it.
Only a majority of the nodes need to update to the new version, while the rest can continue as they are, still able to validate and record transactions.
An example of a soft fork is the Taproot upgrade in the Bitcoin blockchain in November 2021 that improved the efficiency, privacy and smart contract capabilities (Bitcoin doesn’t exactly have smart contracts, but that’s a discussion for another post). Ultimately, this is what enabled Bitcoin ordinals, which we touch on a little later.
Another example is the Ethereum 2.0 upgrade (no longer called that). The Ethereum 2.0 upgrade, also known as Eth2 or Serenity, was a significant upgrade to the Ethereum blockchain that transitioned its consensus mechanism from Proof of Work (PoW) to Proof of Stake (PoS) to improve scalability, security, and sustainability. This transition was implemented through a series of updates, and while it involved fundamental changes to the network’s structure, it was designed to be rolled out in a way that would be compatible with the existing Ethereum blockchain, avoiding a hard fork in the traditional sense. Most users didn’t even realize this was happening.
Hard Fork
A hard fork is more dramatic. It’s a software update that isn’t backward compatible. This means the new path has rules so different that the old version can’t play by them.
When a hard fork occurs, all nodes and users must decide if they will follow the new rules or stick with the old ones. This means updating software. If there’s disagreement, the chain permanently splits into two: one follows the new protocol, and the other stays true to the original code.
An example of a hard fork was when Ethereum (ETH) split from Ethereum Classic (ETC) in 2016 in response to The DAO hack. The Ethereum community was faced with a decision: do nothing and accept the hack, or intervene and reverse the transaction to return the funds. The split represented a fundamental philosophical divide within the Ethereum community. One side valued immutability and the principle that the blockchain should never be altered (this became Ethereum Classic), while the other side prioritized the community’s decision and the need to correct a significant exploit (Ethereum).
Why Forking Happens
Forking usually happens for a few reasons:
- To Upgrade the System: Sometimes, the community wants to add new features or improve the blockchain’s functionality.
- To Correct Security Risks: If a security flaw is found, a fork can be used to fix it.
- Due to Differences in Vision: Sometimes, the community behind a blockchain can’t agree on its future direction, leading to a split.
The Impacts of Forking
When a blockchain forks, it can have various outcomes:
- New Currency: In the case of hard forks, a new cryptocurrency can be created. For instance, Bitcoin Cash (BCH) resulted from a Bitcoin (BTC) hard fork.
- Market Reaction: Forks can lead to uncertainty and volatility in the market as people decide which path they believe has more value.
- Community Division: Forks can divide the community as members take sides, potentially leading to a competition for resources, developers, and users.
Forks are a sign of the democratic and decentralized nature of blockchain technology, where the community governs and decides the course of the platform’s future.
They reflect the flexibility of blockchains to adapt and evolve but also highlight the challenges of consensus within a diverse community.
Okay, we keep talking about the community of a blockchain. You must be asking, why do people want to be part of this? What do they get out of it? Well, they get rewards.
Block Rewards
Going back to our example of a whole class looking at your papers and tests rather than just a teacher, why would a group of teenagers want to look at your assignments? Even more so, why would they want to spend a lot of time looking at them and then grade them?
Well, in this analogy, they would be paid to. In almost every blockchain, you get a reward for participating and putting in valid votes. On the Bitcoin blockchain, you get paid in bitcoin; on the Ethereum blockchain, you get paid in ether… and so on.
Okay, but where does this magical, virtual cryptocurrency come from? How does the blockchain ledger know how many bitcoins there are, for instance? And are more just created to pay the participants?
Cryptocurrency
Whoever solves the math problem of each block and finds the magical hash, they add “[my account] received 2 bitcoins for mining” at the top of the block. This is their mining reward, and it automatically goes into their bitcoin wallet. This is also answers the question “How are Bitcoins are created?“.
Okay, that brings us to the question of how many coins can there be? Can miners or stakers or other participants in the blockchain just keep creating new coins forever?
On most blockchains, the answer to that question is “no”. Bitcoin, for instance, has a cap on how many bitcoins can ever exist: 21 million. This limit is hardcoded into the protocol, ensuring that Bitcoin remains a deflationary asset. The reward for mining a block will keep halving until the maximum supply is reached around the year 2140.
The Halving
Bitcoin has a unique feature where the reward for mining a block is halved every 210,000 blocks, or approximately every four years. This event is known as “the halving”. It’s designed to control the rate at which new bitcoins are created and mimic the scarcity and inflation rate of precious metals like gold.

Other blockchains have different total supply caps. If you’re curious about cryptocurrencies, you should check out our other section about them that goes into far more detail.
A few things are important to know about cryptocurrencies, though, and how they make sure the blockchain works. The primary use-case for cryptocurrencies on most chains is for gas. When you’re driving a car, you need fuel to keep it running. In the world of cryptocurrency, particularly within networks like Ethereum, “gas” serves a similar purpose. It’s not a physical substance, but a virtual unit that powers actions on the blockchain.
Every time you send a transaction or execute a smart contract on the Ethereum blockchain, you need gas to fuel that action. Gas also measures how much computing work is needed to process transactions or smart contracts. And lastly, requiring gas for transactions helps prevent spam on the network. It’s costly to perform many transactions, which discourages wasteful or malicious activity.
How much gas is needed changes based on both the blockchain you’re using and the activity you’re doing on it. Transactions of NFTs, for instance, which hold a lot of on-chain data, will cost more than just sending a friend some ether.
Wait, what’s “on-chain data”? In a blockchain, data can be stored in two main ways: on-chain or off-chain.
On-Chain vs. Off-Chain
On-Chain data is recorded and stored directly on the blockchain, which means:
- Transparency: All transactions are visible to anyone who looks at the blockchain.
- Immutability: Once data is added to the blockchain, it cannot be changed or deleted.
- Security: On-chain transactions are secured by the blockchain’s consensus mechanism, making them very secure.
The downside? Just like bank transactions can take time to process and can have higher fees, on-chain actions can be slower and more expensive, especially when the network is busy.
Off-Chain data is like cash in your wallet. It’s handled outside the blockchain and involves:
- Privacy: Transactions are not publicly recorded on the blockchain, so they’re more private.
- Speed: Off-chain transactions can be faster since they don’t have to go through the blockchain’s consensus process.
- Cost: They are usually cheaper or even free because they don’t require miner fees.
However, because they’re not recorded on the blockchain, off-chain transactions don’t have the same level of security or immutability. They often rely on other trust methods, such as trusted third parties.
Many blockchain applications use a mix of on-chain and off-chain data. They might store essential transaction details on-chain to ensure security and immutability while handling other information off-chain for efficiency and privacy.
A recent example of completely on-chain data is Bitcoin ordinals. Bitcoin ordinals are a way to inscribe unique digital artifacts, such as images or texts, onto individual satoshis (the smallest unit of bitcoin). These inscriptions turn each satoshi into a distinguishable and collectible item, similar to non-fungible tokens (NFTs) on other blockchains. It’s kind of complicated how this works, so we won’t go into more detail here, but you can check out our video about ordinals to help make more sense of it.
You might be asking how blockchains communicate on- and off-chain. Aren’t they self-contained? How can a blockchain coded with a coding language like Solidity know what is happening on the stock market, for instance? Through something called oracles.
Oracles
Oracles act as a bridge between the digital and real worlds. They bring external data into the blockchain environment by providing smart contracts with external information.
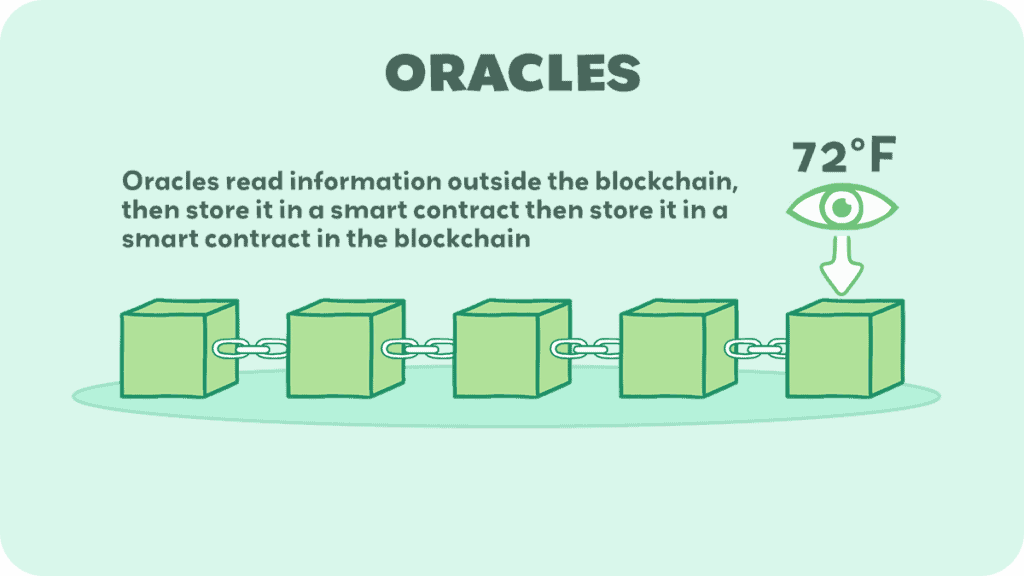
Here’s how they work:
- Oracles fetch data from the outside world. This could be anything from temperature readings to stock prices or flight times.
- The data provided by oracles can tell a smart contract to do something. For instance, a smart contract for crop insurance might use data from an oracle about weather conditions.
There are three types of oracles:
- Software Oracles: These handle online data like exchange rates, flight information, or weather forecasts.
- Hardware Oracles: They interact with the physical world, like RFID sensors in supply chains.
- Consensus-based Oracles: These gather data from multiple sources to reach a consensus, ensuring data reliability.
You might be thinking, “Okay, I get that cryptocurrency has more purposes than just a type of money. But how does someone access cryptocurrencies in the first place?” The answer is simple: cryptocurrency wallets.
Crypto Wallets
There are two primary types of wallets: hard (otherwise known as cold) wallets and soft (otherwise known as hot) wallets.
Hard wallets are physical hardware devices that you connect to via a USB stick or similar connection. They exist offline and are considered the most secure wallet.
Soft wallets are digital software wallets that function primarily online either as an app you download or a browser extension.
The most important thing to know about any crypto wallet is that you need to have your own private keys, otherwise you do not have what we call “self-custody,” meaning you’re not in control of your own assets.
The opposite of self-custody is keeping your crypto in an exchange like Coinbase or Binance. In exchanges, you don’t have your own private keys, which means that Coinbase and Binance ultimately have control over your wallet. It means that if something happens to the exchange, like they were misusing customer funds, you have no way of getting your crypto back.
So, all wallets have both private and public keys. It’s a little too complicated to go into detail about here, but know that you should NEVER share your private key with anyone. You should store it offline, somewhere safe where no one else can find it. Your public key, however, can be given out freely and is how people will know where to send you coins and tokens.
It’s kind of like the difference between sharing your home address and giving someone the key to your front door. Your public address is safe for people to know (probably), but your key is something they should never have.
Trading and Selling
Why do you need addresses? Well, to send and receive crypto, of course. Not to mention they are now used for identity, games, logins, emails, and a number of other things.
We get into this more in the “DeFi” section of our site, but will touch briefly on some important blockchain-tech-specific concepts here.
Most people can just send and receive coins and tokens on the same blockchain to other addresses on the blockchain. Say I want to send you 2 bitcoin. As long as I am using a bitcoin wallet and you give me a bitcoin address, all I have to do is go to the “send” feature in the wallet, put your address in, and voila, you get it the bitcoin as soon as the blockchain can process the transaction.
If you want to send coins or tokens across different blockchains, you first have to bridge to the new network, which is something you can’t really do with bitcoin, but we explain that in the “DeFi” post. So for an example, if I want to send you 2 ether but the gas is too expensive and you don’t want to use the main chain for future transactions, I can bridge the ether to a layer 2 Ethereum-compatible chain like Polygon and send you the 2 wrapped ether on Polygon instead.
That was kind of complicated. A wrapped token is a token that is not native to the blockchain it is on, but is a representation of a different native coin. Remember, a coin is the cryptocurrency that helps run the blockchain by paying gas fees etc. A token is a cryptocurrency that is on the blockchain but is not necessary for the blockchain to function. So, wrapped ether on Polygon is a representation of ether on Ethereum. You can watch our video about wrapped tokens to help understand it better.
That’s kind of complicated though, right? First, you have to own the main crypto, then you have to figure out which blockchain people are using and make sure you can bridge the coin/token to the other blockchain if needed, and then send it. There’s another way to send crypto that’s more directly, but you have to know how to do it, and it’s called atomic swapping.
Atomic Swaps
Atomic swaps are a blockchain technology that allows two parties to exchange different cryptocurrencies directly and securely, without the need for a trusted third party, like an exchange.
Imagine you have Bitcoin, and you want to trade it for Ethereum with someone. Normally, you’d both have to trust an (centralized or decentralized) exchange to make this trade. But with an atomic swap, you can make this exchange directly with the other person, securely and instantly. Here’s a simplified view of how it works:
- Smart Contracts: The swap is powered by smart contracts, which are like automated agreements written in code.
- Hashed Time-Locked Contracts (HTLCs): Both parties submit their transaction to this type of smart contract. Each party sets a secret key and a time limit for the transaction.
- Transaction Process: For the swap to be successful, both parties must confirm their transaction within the set time frame. If one party doesn’t confirm, the smart contract cancels the transaction, and the funds are returned.
- Finalization: Once both parties confirm and the conditions are met, the swap is automatically executed, and the currencies are exchanged.
Benefits of Atomic Swaps
- Decentralization: They reduce the need for centralized exchanges, aligning with the ethos of blockchain technology.
- Security: The risk of theft or fraud is minimized as the swap happens directly between two parties and is governed by the immutable conditions of the smart contract.
- Reduced Costs: By cutting out intermediaries, atomic swaps can also reduce transaction fees.
Challenges and Considerations
- Compatibility: Not all cryptocurrencies support the technology needed for atomic swaps.
- Liquidity Issues: Atomic swaps require finding a matching party who wants to trade the exact amount of the opposite cryptocurrency, which can be a challenge.
- Technical Complexity: Setting up and executing atomic swaps requires a good understanding of blockchain technology and smart contracts.
How to Get Cryptocurrency
We kind of jumped the boat there, explaining how to send and receive crypto. First, you need to get some crypto, right?
If you’ve read this whole thing already (and kudos to you if you have!), you know that the people who help maintain the blockchain are rewarded in crypto for their work. But that’s not the only way to get crypto. You can also buy it.
We mentioned crypto exchanges earlier, which are centralized entities similar to banks that will sell you crypto for a (usually small) fee. That’s how most people get crypto, however there are also decentralized exchanges that allow you to purchase crypto using third-party payment companies.
There are also other ways to get crypto “for free”, including faucets, airdrops, and initial coin offerings (ICOs).
ICOs are illegal in a lot of places now, but briefly, they are when a new community gives a bunch of their tokens to early investors. Sometimes ICOs make you buy their coin/token, and other times they just give it freely to people who helped build or invest in the development of the project.
A quick side note: we have mentioned coins and tokens a few times now but haven’t really explained the difference. A coin is a blockchain’s native asset. Bitcoin’s coin is bitcoin. Ethereum’s coin is ether. Some blockchains are able to hold smart contracts, like Ethereum, which means people can create their own tokens on the network. These tokens can be anything from a simple asset like USDC (a stablecoin), or as complex as an audio-visual non-fungible token (NFT).
Airdrops are when a token is distributed to people based on their activity on the blockchain, in the Decentralized Autonomous Organization (DAO), or purchase of an NFT. An example is a famous airdrop by the Arbitrum layer 2 blockchain where the early users of the chain received anywhere between a couple hundred up to $20,000 worth of the ARB token.
Faucets are another way to get free crypto, but they tend to be really small amounts, like fractions of a penny. Faucets are meant to give people gas so they can perform transactions on a blockchain. For instance, a MATIC faucet would give you just enough MATIC to perform a transaction on the Polygon network. At the time of writing this article, the average gas fee on Polygon is less than one cent. So, faucets aren’t a way to make money, really.
The thing to note about free stuff, especially free crypto, is that it isn’t usually actually free. Usually, ICOs and airdrops require you to have done things already, which means you need to put money in to get it. And faucets are only meant to give you enough to perform transactions, which means you need to have crypto on the chain already. Anything that says it’s completely free is probably a scam.
There’s a lot to unpack about how to get crypto and the various use-cases for it, so we won’t get too far into it here since we have a whole page dedicated to cryptocurrencies. Just know that there are various methods, some safer than others, and that it’s important to know how to store it (hard or soft wallet) to keep it safe.
An important thing to keep in mind, although kind of adjacent to cryptocurrency specifically, is the idea of a commodity vs. a security. These are important concepts in finance that have impacts on cryptocurrency regulations, and what cryptos are “safe” to buy or not, depending on your jurisdiction.
Commodity vs Security
Simply put, a commodity is a basic good used in commerce that is interchangeable with other goods of the same type. These are often natural resources or agricultural products.
On the other hand, a security is a financial instrument that represents some type of financial value. It often signifies ownership in a publicly-traded corporation (stock), a creditor relationship with a governmental body or a corporation (bond), or rights to ownership as represented by an option.
Why do we think you need to know this? The question of whether cryptocurrencies are securities is a complicated debate in the financial and legal realms. The classification of a particular cryptocurrency as a security can have significant regulatory and legal implications.
The specific definition of a security is an investment of money in a common enterprise with an expectation of profit derived from the efforts of others. This definition comes from the U.S. Supreme Court’s “Howey Test,” established in the 1946 case SEC v. W.J. Howey Co.
Some cryptocurrencies might meet the criteria of being a security, especially those that resemble traditional investments like stocks or bonds. For example, if a digital token is sold to investors to raise capital for a project and the investors expect to earn a profit from the efforts of the project’s creators, it could be considered a security (this is an example of many ICOs, like we mentioned earlier).
A prominent example of how this can play out legally is the recent multi-year legal battle between Ripple Labs and the SEC, where the SEC alleged that Ripple’s XRP token was a security. This case is closely watched as it could set a precedent for how other cryptocurrencies are treated by regulators.
If a cryptocurrency is deemed a security, it must comply with specific registration and disclosure requirements, which can be complex and costly. Cryptocurrencies can be broadly categorized into utility tokens and security tokens. Utility tokens provide users with access to a product or service and are not designed as investments; security tokens are akin to digital shares in a company. Whether a cryptocurrency is considered a security depends on its specific characteristics and the legal framework of the jurisdiction in question.
And that brings us into a rather philosophical realm. Different governments around the world are treating cryptocurrencies differently, and regulations are inconsistent. There doesn’t seem to be one right answer to this problem, at least not yet.
Blockchain Philosophy
Okay. We’ve gone over what a blockchain is, when the idea started, how they work, and who can (and should) participate. Let’s take a look at the reasons for blockchains to exist in the first place.
Basically, these reasons include trust, transparency, immutability, inclusivity, and efficiency.
It also includes some other things. We mentioned decentralization earlier. It’s a really fundamental part of the blockchain ethos, along with two other things: security and scalability. These three things make up the blockchain trilemma.
Blockchain Trilemma
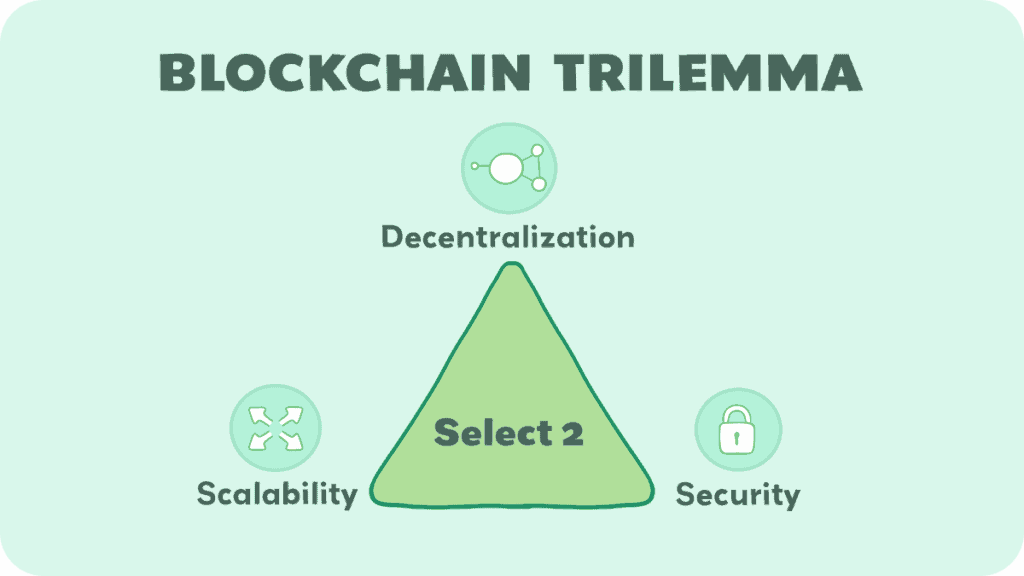
The term was coined by Ethereum co-founder Vitalik Buterin. It refers to the challenge of achieving three main objectives simultaneously: security, scalability, and decentralization. Here’s a breakdown:
Security
This is about protecting the network from attacks and ensuring that every transaction is accurately recorded without any alterations. Security means that the system is robust against fraud, hacking, and other malicious activities.
Scalability
Scalability involves the blockchain’s ability to handle a large number of transactions quickly and efficiently. As more people use the blockchain, it must grow its capacity to process transactions without lagging or becoming too expensive.
There are many methods to achieve scalability, including different ways to manage ledgers and the data in them. More nodes will mean more scalability. One of the methods to scale is called sharding. Sharding divides the blockchain into smaller, more manageable pieces called “shards.” Each shard contains its own independent piece of the blockchain’s state, which means its own set of account balances and smart contracts.
Decentralization
Decentralization is the idea that the control and maintenance of the blockchain are spread out across various parties rather than being controlled by a single entity. This spreads out power and ensures that no single party can control or manipulate the system for their own benefit.
The trilemma suggests that blockchains must balance these three pillars. However, prioritizing one often means compromising on another.
For instance, a highly secure and decentralized blockchain may not scale well, leading to slower transactions and higher costs. Conversely, increasing scalability might require more centralized solutions, which could compromise security and the decentralized nature of the blockchain.
Solving the blockchain trilemma is one of the key challenges faced by developers and innovators in the field. Different blockchain projects prioritize different aspects, leading to a variety of networks with different features and trade-offs.
This leads us to ask what other aspects different blockchains are interested in.
Trust
Blockchains enable what is called a trustless environment where people can transact directly with each other without needing to trust one another; the trust is placed in the system’s code and the decentralized network of participants who validate transactions.
We’ll talk about the code a little later, but keep it in mind because it’s really important.
Since the entire blockchain is transparent, meaning that all activity on it can be checked and confirmed by anyone who wants to see it, there’s no reason to trust that someone will do what they say they’ll do—you can verify it yourself.
And, importantly, the blockchains are immutable, which means they can’t be changed. This is both good and bad—good because someone can’t say “but I did pay you this” and create a fake receipt, for instance, and bad because if you made a mistake and sent your coins somewhere wrong, you can’t get them back.
Empowerment
Blockchains can empower individuals by giving them control over their own data and financial assets. It provides tools for identity management, ownership, and personal data sovereignty.
Those were big words, but basically it just means that users don’t have to rely on governments or banks to decide whether or not they are allowed to make a transaction, or send a message, or anything else a blockchain lets you do.
Blockchain removes the need for this central authority, distributing the control across a network, which can help reduce points of failure and risks of corruption. You can’t bribe someone on the blockchain to fake a transaction saying you have a million dollars, because it isn’t just up to them.
This also means that ever person has an equal voice and equal access (for the most part; there is some concern about cost of entry but that’s a bit out of the scope for this article). Because control is distributed among many nodes rather than centralized, it’s much harder for any one person or agency to censor or restrict access to information or services on the blockchain.
By allowing peer-to-peer transactions globally without the need for intermediaries like banks, blockchains can provide financial services to the unbanked and underbanked populations, making sure that everyone has access to the economy.
Efficiency
Blockchains eliminate intermediaries like banks and make it super simple to send money or information between two people. They also work at all hours of the day, every day of the year. So we don’t need to wait for the bank to open on Monday to pay our friend back for the pizza they bought us on Friday night.
If you’ve ever tried to send money internationally, you’d know that it can take MONTHS for the money to get to the right place. With blockchain tech, it happens in a matter of seconds, minutes, or—at the very most—hours.
Transactions with a bank or credit card can also be really expensive. They also try to get you with all those hidden fees. A blockchain doesn’t have hidden fees (a cryptocurrency exchange might, but that’s a conversation for another post). And, a blockchain will be loads cheaper than any other kind of transaction… unless you’re trying to buy NFTs at the height of the bull market (sorry for those of you who weren’t here in 2021… but those fees left a scar on most of us).
Basically, blockchains let us take back control of not just our assets, but our choices, too.
Having said all that, there are a ton of crypto scams out there, so be careful not to get too caught up in the ethos and forget to check the fundamentals of a project before you decide to invest or get involved.
Applications Beyond Cryptocurrency
When you hear “blockchain,” you might immediately think of cryptocurrencies like Bitcoin. And so far that’s mostly what we’ve talked about. But the technology has potential far beyond digital money.
Supply Chain Management
For supply chains, blockchain tech is a truth-teller. It tracks goods from factory to shelf, so you know your organic coffee is really organic. This isn’t just good for your peace of mind; it’s also great for companies who want to prove their ethical practices.
Identity Verification
Blockchain can also act as a digital ID. Instead of juggling passwords, your identity could be a unique digital fingerprint. This could make everything from opening bank accounts to crossing borders simpler and more secure.
Healthcare
Imagine a world where your medical records are safe, yet accessible to every doctor you visit, no matter where. Blockchains can secure sensitive health data and ensure it’s only seen by the right eyes.
Real Estate
Buying property involves piles of paperwork and layers of bureaucracy. Blockchain could store property records, streamline the process, and even enable smart contracts that make buying a house as easy as clicking a button.
Voting Systems
Voting with blockchain could mean saying goodbye to election fraud and hello to democracy in digital form. Your vote would be a secure, anonymous blip in the blockchain, making sure every voice is counted without compromise.
Artificial Intelligence
The merging of cryptocurrency and artificial intelligence (AI) is a growing area of technology and has created a ton of hype. AI can enhance blockchains by improving security through pattern detection, optimizing the energy use in crypto mining, and powering smart trading algorithms. In the other direction, blockchains can help AI by securing data and facilitating the sale and use of personal data in a transparent way.
In each of these cases, blockchain technology provides a level of security and transparency that was previously unimaginable. Blockchain isn’t just for techies and traders—it’s a new way of thinking about how we share, verify, and record the truth in all areas of life. And if you can imagine it, it can probably exist. Whether it should exist is a different question.
Conclusion
So in conclusion, blockchains can be simple ledgers or more complicated “trains” of data movement and execution. They are distributed networks of nodes that any person or company can help maintain. They are made secure by miners, stakers, or other consensus mechanisms that use cryptography. The hash that secures each block can work as a privacy-enhancing “lock” on the data or just to prove that the block is in the right order and is verified as being accurate.
The idea of blockchains began in the 1990s but wasn’t fully implemented until 2008 when the Bitcoin blockchain was launched.
There can be many layers to a blockchain that allow it to handle the trilemma problem of scalability, security, and decentralization, more efficiently. Layering isn’t just important for blockchain functionality specifically, but also useful for the non-cryptocurrency specific use-cases, such as AI, identity or supply chain management.
Still, the largest use-case for blockchains right now is still in cryptocurrency, which people can purchase on centralized or decentralized exchanges, exchange with other people, or invest in interesting ways to try to make money.
That was an awful lot of information, so if you made it all the way here, we applaud you, and thank you very much for taking the time. If you have any questions, hop into our public Discord channel and ask away!